How to sanitise a Cisco IOS configurations?
Cisco IOS configurations are text files, including the configuration data of devices. It also includes sensitive information, such as Passwords, IP addresses, pre-shared keys and other type of keys.
In different situations we need to share the configuration with others, so they can understand the solution and/or use configuration details. Perhaps the customer would like to see the to-be configurations to approve a change, or in case request for professional services from a company, they need to understand the configuration in more details.
Removing the sensitive information from Cisco configurations is a good use-case for using Automation.
Fortunately, there is a library from Intentionet we can use: Netconan. This was briefly mentioned before in this post, however let's see it in action now.
Installation of Netconan
To install Netconan we just need to execute the following command:
pip install netconan
I have used this CVD configuration pack to try out netconan. I have created a folder, and enabled GIT to see what has been changed by netconan.
(netconan) area-x51:Netconan_blog_post xcke$ ls -la
total 0
drwxr-xr-x 5 xcke staff 160 Dec 8 14:14 .
drwxr-xr-x 40 xcke staff 1280 Dec 8 14:07 ..
drwxr-xr-x 12 xcke staff 384 Dec 8 14:14 .git
drwxr-xr-x 5 xcke staff 160 Dec 8 14:16 clean_configs
drwxr-xr-x 5 xcke staff 160 Dec 8 14:14 original_configs
Original configurations are stored in a folder, and I have created a folder for the sanitised configurations. To start netconan, lets use the following command:
netconan -i original_configs/ -o clean_configs/ -anonymize-passwords
We have used the “—anonymize-passwords” flag to ask Netconan to change the passwords, SNMP community strings, etc. Standard password and hash formats (salted md5, Cisco Type 7, Juniper Type 9) are recognised and substituted with format-compliant replacements.
Looking at GIT, we can see the changes in different sections of the configuration.
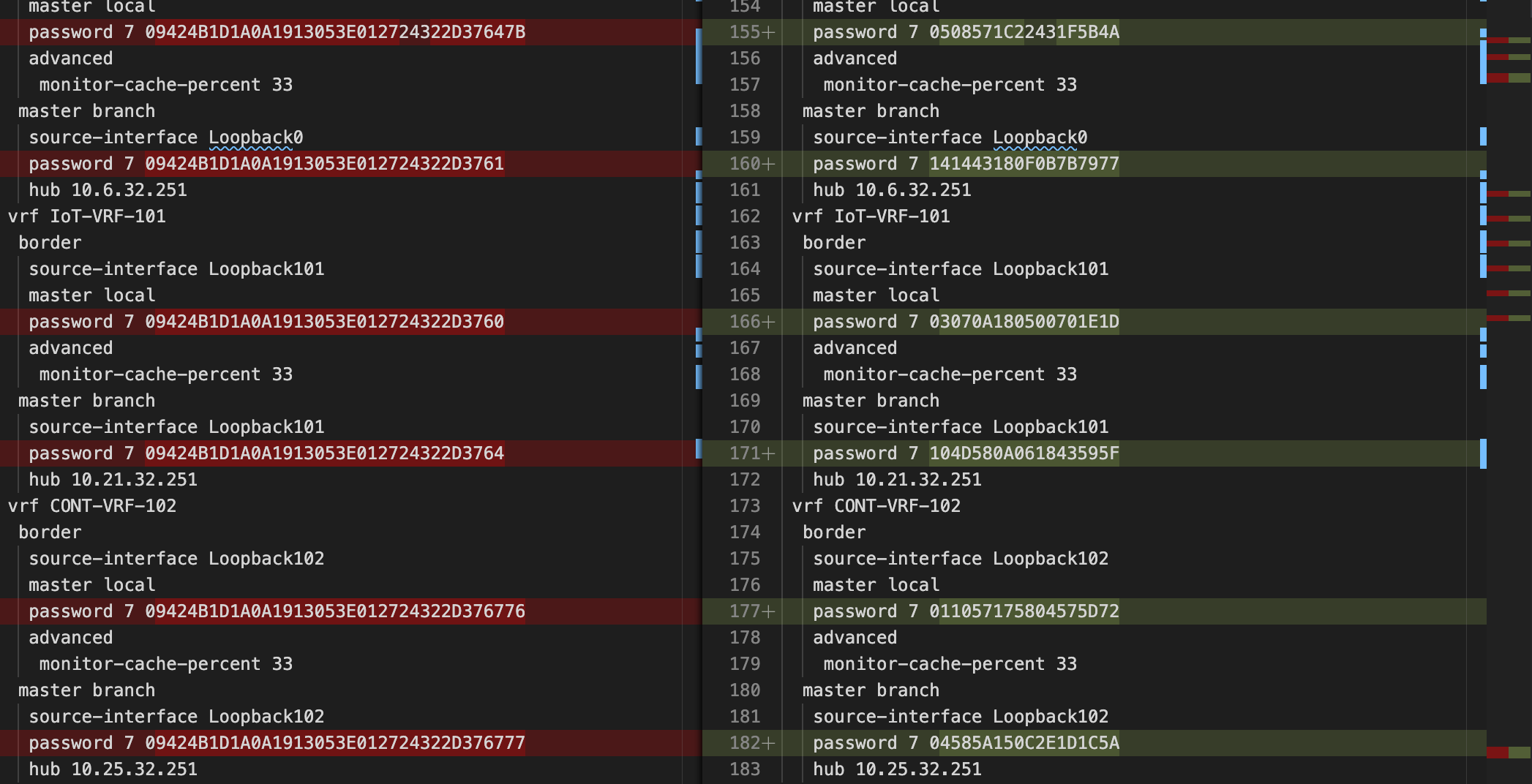
All the password related information changed. However, we can also ask netconan to anonymize IP information.
netconan -i original_configs/ -o clean_configs/ --anonymize-passwords --anonymize-ips
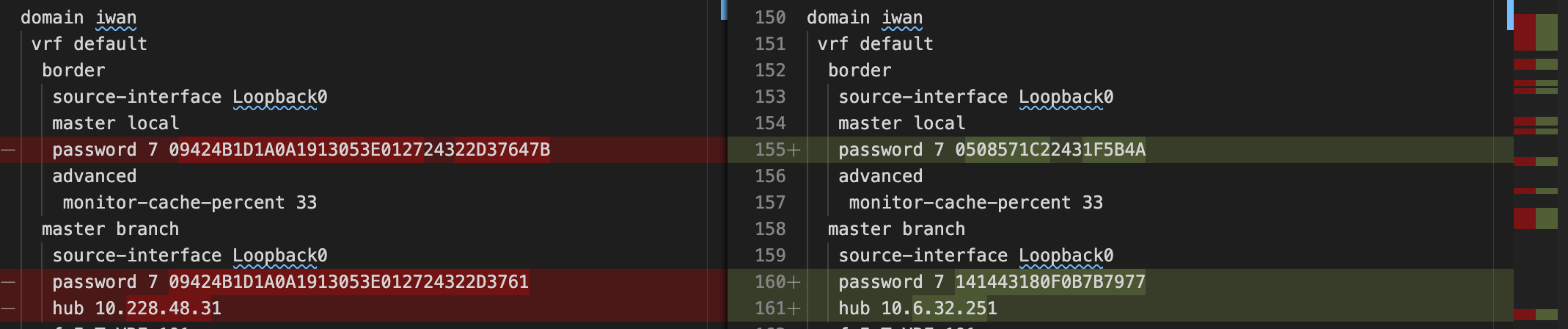
Netconan preserves prefixes when anonymizing IPv4 and IPv6 addresses. IP addresses with a common prefix before anonymization will share the same prefix length after anonymization.IPv4 classes and private-use prefixes are preserved by default also, but can be overridden with --preserve-prefixes (e.g. --preserve-prefixes 12.0.0.0/8 will preserve a leading octet 12 of IP addresses encountered but anonymize octets after the 12)
There are a number of other use-full features we can use:
- Provide a list of sensitive words that Netconan will anonymize.
- Provide a list of words that should not be changed by netconan
- Input a list of comma separated AS numbers to anonymize
Netconan is a simple tool to remove sensitive information from text based configurations. It can be customized and tailored to different use-cases. It is also a good example of using simple automation in configuration management.
